Embarking on the journey of cybersecurity best practices, we delve into the crucial aspects that ensure the safety and protection of both individuals and organizations in the digital realm. From understanding the risks to implementing proactive measures, this topic sheds light on the essentials of cybersecurity.
Importance of Cybersecurity Best Practices
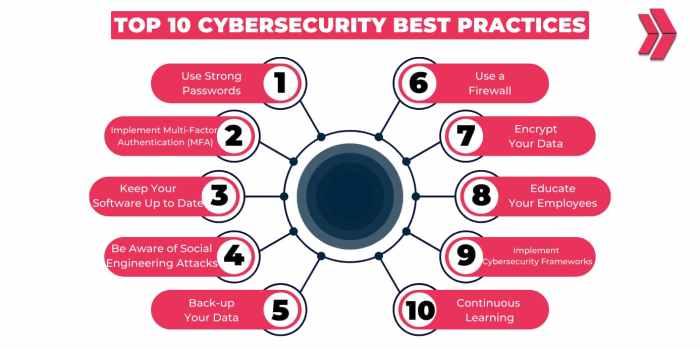
Implementing cybersecurity best practices is crucial for both individuals and organizations to safeguard sensitive information, prevent data breaches, and protect against cyber threats.
Mitigating Risks and Threats
By following cybersecurity best practices, individuals and organizations can mitigate various risks and threats, such as:
- Unauthorized access to confidential data
- Malware infections and ransomware attacks
- Phishing scams and social engineering tactics
- Data theft and identity theft
Impact of Non-Compliance
Failure to adhere to cybersecurity best practices can have severe consequences, including:
- Financial losses due to data breaches and fraud
- Damaged reputation and loss of trust from customers
- Legal implications and regulatory fines for non-compliance
- Disruption of business operations and loss of productivity
Core Principles of Cybersecurity Best Practices
In the realm of cybersecurity, there are several core principles that serve as the foundation for implementing effective best practices. These principles are essential for safeguarding sensitive information and preventing cyber threats from compromising systems and data.Defense in Depth:Defense in depth is a fundamental principle that involves creating multiple layers of security defenses to protect against a variety of potential threats.
By implementing a combination of technical, physical, and administrative controls, organizations can establish a robust security posture that reduces the risk of successful cyber attacks.Least Privilege:The principle of least privilege dictates that individuals should only be given access to the information and resources necessary to perform their job functions.
By limiting user permissions to the minimum required level, organizations can minimize the potential damage that can be caused by insider threats or compromised accounts.Continuous Monitoring:Continuous monitoring is a proactive approach to cybersecurity that involves regularly monitoring systems, networks, and data for signs of suspicious activity or potential security breaches.
By maintaining real-time visibility into the security posture of an organization, security teams can quickly detect and respond to threats before they escalate into significant incidents.Proactive Cybersecurity Measures:Proactive cybersecurity measures involve anticipating potential threats and taking preemptive action to prevent security incidents from occurring.
This approach includes conducting regular risk assessments, implementing security controls based on best practices, and staying informed about emerging threats and vulnerabilities.Different Approaches to Implementing Cybersecurity Best Practices:There are various approaches to implementing cybersecurity best practices, each with its own strengths and weaknesses.
Some organizations may prefer a risk-based approach that focuses on identifying and prioritizing the most critical assets and vulnerabilities, while others may opt for a compliance-driven approach that aligns with regulatory requirements and industry standards. Ultimately, the most effective approach will depend on the unique needs and risk profile of each organization.
Implementing Cybersecurity Best Practices
Implementing cybersecurity best practices is crucial for organizations to protect their sensitive data and systems from cyber threats. Creating a cybersecurity framework, training employees, and utilizing tools and technologies are essential steps in this process.
Creating a Cybersecurity Framework
A cybersecurity framework Artikels the organization's approach to managing cybersecurity risk. Here are the steps involved in creating one:
- Identify and assess the organization's assets, vulnerabilities, and potential threats.
- Develop policies and procedures to address cybersecurity risks and establish security controls.
- Implement security measures such as encryption, access controls, and monitoring tools.
- Regularly review and update the framework to adapt to evolving threats and technologies.
Training Employees on Cybersecurity Best Practices
Employee training is essential to ensure that everyone in the organization understands and follows cybersecurity best practices
- Provide regular cybersecurity awareness training to educate employees on common threats and how to prevent them.
- Conduct simulated phishing exercises to test employees' awareness and response to phishing attacks.
- Encourage employees to report any suspicious activity or potential security incidents promptly.
Tools and Technologies for Implementing Cybersecurity Best Practices
There are various tools and technologies available to help organizations implement cybersecurity best practices. Some examples include:
- Firewalls: to monitor and control incoming and outgoing network traffic.
- Antivirus software: to detect and remove malware from systems.
- Intrusion detection systems (IDS): to identify and respond to potential security breaches.
- Security information and event management (SIEM) tools: to centralize and analyze security event data.
Common Cybersecurity Best Practices
Regular software updates and patches are crucial in maintaining the security of your systems. These updates often include important security fixes to vulnerabilities that cybercriminals could exploit to gain unauthorized access to your data.
Importance of Regular Software Updates and Patches
- Regular updates protect your systems from known security threats.
- Updates fix bugs and issues that could potentially be exploited by hackers.
- By staying up-to-date, you ensure that your systems have the latest security features and protections.
Significance of Strong Password Policies and Multi-Factor Authentication
- Strong password policies help prevent unauthorized access to your accounts and systems.
- Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before granting access.
- Combining strong passwords with multi-factor authentication significantly reduces the risk of unauthorized access.
Best Practices for Securing Network Infrastructure and Data Storage
- Secure your network with firewalls, intrusion detection systems, and regular network monitoring.
- Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Implement access controls to restrict user privileges and limit exposure to sensitive information.
Concluding Remarks
As we reach the conclusion of this discussion on cybersecurity best practices, it becomes evident that adherence to these principles is paramount in safeguarding against cyber threats. By following the core principles and implementing the necessary strategies, individuals and organizations can enhance their cybersecurity posture and mitigate potential risks effectively.
Expert Answers
How often should software updates be performed?
Software updates should ideally be performed as soon as they are available to patch any vulnerabilities and ensure the security of systems.
What is the importance of multi-factor authentication?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple credentials for access, reducing the risk of unauthorized entry.
How can network infrastructure be secured effectively?
Securing network infrastructure involves implementing firewalls, encryption, regular monitoring, and access controls to protect against cyber threats.